
Phishing and spoofing - The use of email and online messaging services to convince victims to share personal data, login credentials, and financial details.
Data breach - Stealing confidential, protected, or sensitive data from a secure location and moving it into an untrusted environment consists of stolen data from users and organisations.
Denial of service (DoS) - Disrupting the traffic to an online service, system, or network with malicious intent.
Malware - Malicious software that damages or disables a user's device or by stealing personal and sensitive data.
Ransomware - Malware that prevents users from accessing critical data and then demanding payment in the promise of restoring access. Ransomware is typically delivered via phishing attacks.
Business email compromise (BEC): A sophisticated attack that targets businesses that operate on wire payments. It compromises legitimate email accounts through social engineering techniques to submit unauthorised charges.

The hacker first compromises a legitimate website or creates a fake website. Then, they acquire a list of email addresses to target and distribute an email message that aims to dupe people into clicking on a link to that website. When a victim clicks the link, they are taken to the website, either requesting a username and password or automatically downloading malware onto their device that steals sensitive information. The hacker can use this data to access a user's online account, steal more data like credit card details and corporate access networks attached to the device or commit wider identity fraud.
Email phishing scammers will often express the need for urgency from their victims. This includes telling them that their online account or credit card is at risk and that they must log in immediately to rectify the issue.
Greeting card scams
Many internet fraud attacks focus on popular events to scam the people celebrating them. This includes birthdays and festive occasions, commonly marked by sharing greeting cards with friends and family members via social media. Hackers typically exploit this by installing malicious software within the greeting card, automatically downloaded into the recipient's device when they open the card.
The consequences can be devastating. The malware takes the form of annoying pop-up ads that affect an application's performance on a smart device. However, the more worrying outcome would be the victim's personal and financial data being stolen and their computer being compromised as a bot within a vast network of computers, also known as - a 'botnet.'

Lottery fee fraudsters typically craft emails to look and sound believable, which still results in many people falling for the scam. The scam targets people's dreams of winning massive amounts of money, even though they may have never purchased a lottery ticket. Furthermore, no legitimate lottery scheme will ask winners to pay to claim their prize.

The scam uses a premise of a wealthy Nigerian family or individual who wants to share their wealth in return for assistance accessing their inheritance. They use phishing tactics to send emails that outline an emotional backstory, then lure victims into a promise of significant financial reward. The scam typically begins by asking for a small fee to help with legal processes and paperwork with the promise of a large sum of money further down the line.
The scammer will inevitably ask for more extensive fees to cover further administration tasks and transaction costs supported by legitimate-looking confirmation documents. However, the promised return on investment has yet to arrive.
Macau scam
These fraudsters are pretending to be Malaysian Law enforcement agencies such as the - PDRM, LHDN, MCMC, MACC, and the latest scammer tactic, is reported to be calling from – POS Malaysia's express delivery service - POSLAJU.
The MO starts with a call and will convince the victims about the crime they have committed. Hence, they will give their Bank User ID and Password out of fear and release the TAC [Transaction Authorisation Code] to these criminals. Once this information is released, the victim's savings are withdrawn through cash advances through an ATM or transferred to another mule account.
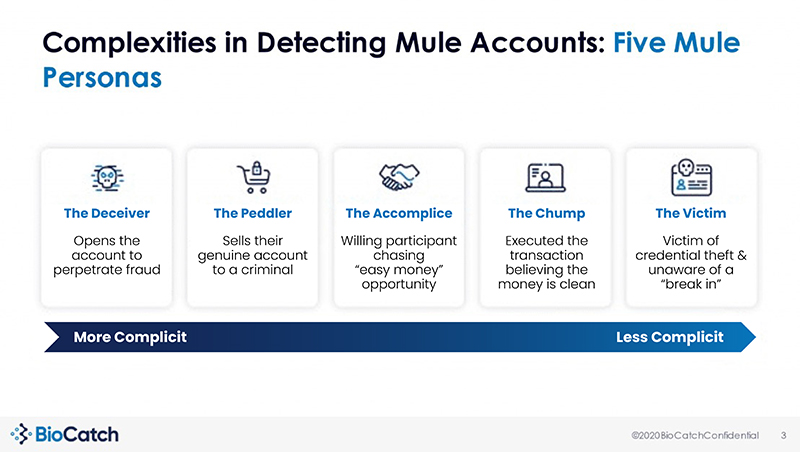
Decrypting mule account holders and their intent
A mule account is an account that belongs to an individual or company, which allows their bank account to be controlled and used by criminals. It works by handing over an automatic teller machine (ATM) card's PIN or by providing access to online banking credentials to criminals who will then receive money from fraudulent activities. These accounts are offered at RM1,000 per week for renting their account.
Mule account holders can be charged under Section 424 of the Penal Code for fraudulently concealing money. It carries a sentence of imprisonment up to five years, a fine, or both upon conviction, even if such mule account holders are not directly involved in whatever their "renter" does.

Methods of hacking Android operating systems and how it works:
Generates a malicious payload with MSFvenom and extracts it as an APK file.
Injects malicious payloads on legitimate android apps with MSFvenom.
Both methods will require access to the victim's phone or some form of social engineering on the attacker's part to get their victims to install the malicious APKs on their phones.
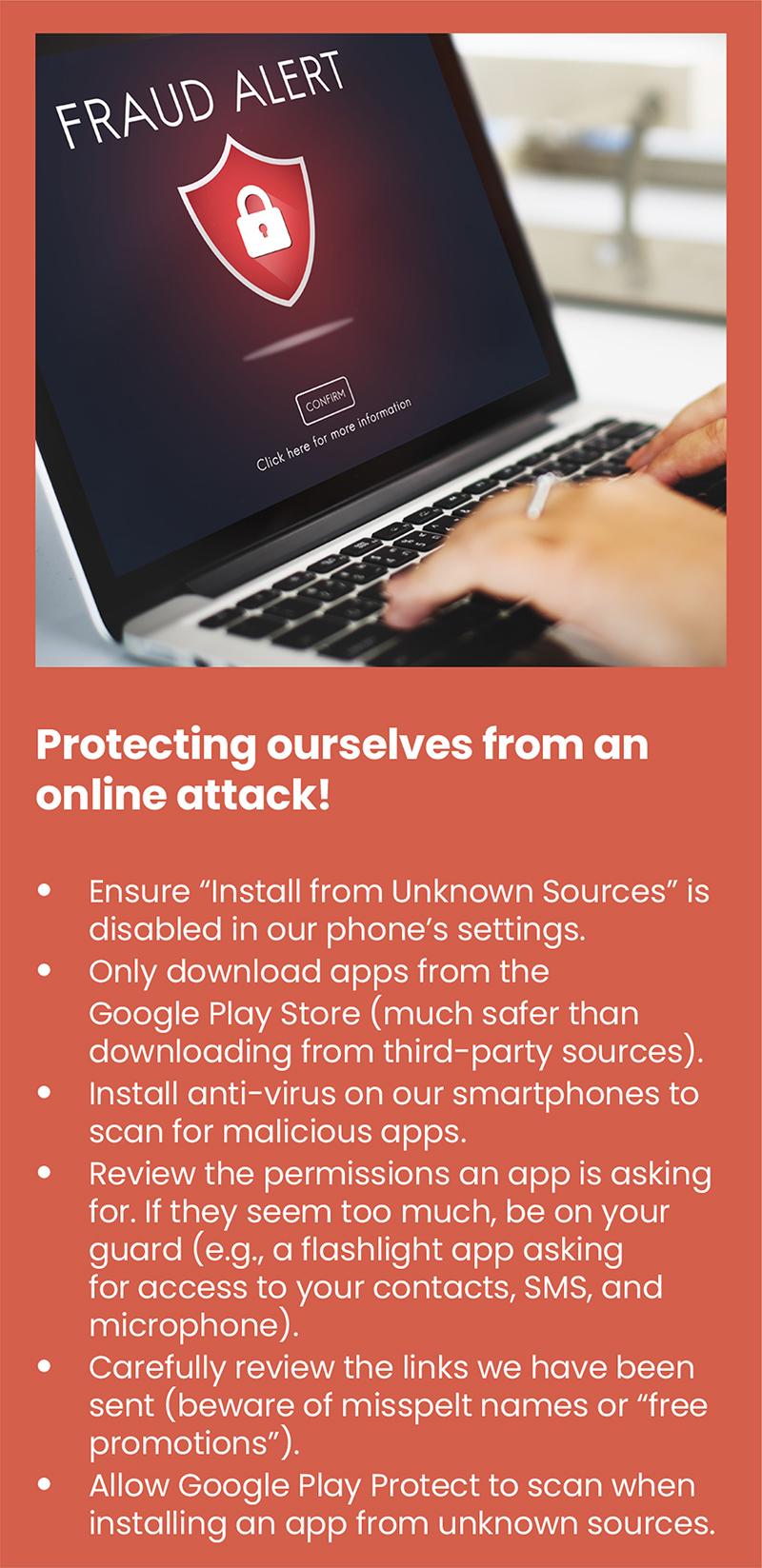

Safeguarding from Internet scams
By remaining vigilant of the common types of internet fraud listed above, Internet users can protect themselves and avoid being caught in a phishing line. It is vital to never send money to someone met over the internet and never share personal or financial details with individuals who are not legitimate or trustworthy. Never click on hyperlinks or attachments in emails or instant messages. Once targeted, internet users should report online scammer activity and phishing emails to the authorities. Check all accounts through PDRM's website for every unknown transfer is better.
Credit card fraud can also be avoided by keeping a close eye on bank accounts, setting up notifications on credit card activity, signing up for credit monitoring, and using consumer protection services. In addition, users who suffer credit card fraud must report it to the relevant legal authorities and credit bureaus.
